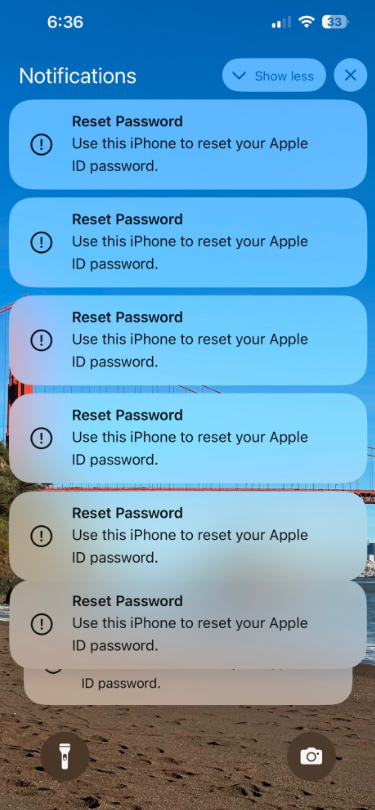
Over the past few days, Apple device users have been exposed to a new wave of phishing attacks called “MFA Bombing” that targeted all Apple devices , including iPhones, Mac computers, iPads, and even Apple smart watches, by flooding the user with notifications asking them to… Change your Apple ID password.
A report by security expert Brian Krebs was based on the statements of people who were targeted, and many Apple device users reported that they had received a large number of notifications requesting their permission to change their account password across all their devices, which constituted a state of great inconvenience, because the user could not use his device normally. Unless you click on all of these notifications and get rid of them.
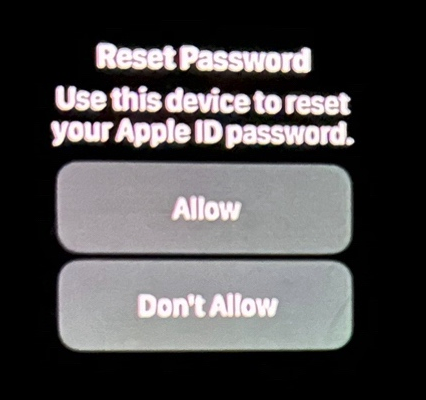
Krebs’ report published on his blog reviews how victims are hunted in this way. When the user receives these notifications, he must interact with all of them, one by one, by clicking on the notification, and then clicking on one of two options: “Allow” or “Allow.” Don’t Allow.
In his report, Krebs mentioned the case of a user called Parth Patel, and what happened to him in this attack via the
The hacker’s goal in this process is for the user to make a mistake and, after being inundated with these notifications, accidentally press the “Allow” button, which will allow the attacker to reset the Apple account password, thus granting him access to the account.
But even if the huge number of notifications do not succeed in confusing the user to press the allow button, the attackers will resort to the second stage, especially if they know the user’s phone number, as the next step will be for the hacker to impersonate an Apple customer service employee, and make a phone call to The user, to inform him that the company has noticed that his account has been subjected to hacking attempts, and to secure the account and change the password, he will request to obtain the temporary code that the user obtained in a text message on his phone.
When this trick succeeds, and the hacker obtains the temporary code, he will use it to complete the process of changing the account password. Once he succeeds in this process, he will access all the user data in the account, and he can permanently expel the user from all devices registered with this account. He can also delete all the data in this account. devices remotely.
In the case of the user Patel, who shared what happened with him, he said that he received the call, but he was very skeptical because the caller asked him for the temporary code that Apple sends, and knowing that Apple does not require those codes, he asked the caller to verify some information about him, and surprisingly, the caller gave him accurate information. Very well, except for his real name.
Patel says that when he asked the caller to verify the name in his Apple account file, the caller gave him a name that was not his real name but a name that Patel had only seen in leaked data reports for sale through a people search website called PeopleDataLabs.
Another client, Chris, a cryptocurrency hedge fund owner, told Krebs he encountered a remarkably similar phishing attempt in late February.
Chris said: “The first alert I received, I pressed ‘Don’t allow’ but immediately after that I received almost 30 other notifications in a row (and added) I thought maybe I sat on my phone, or I was accidentally pressing some buttons that were causing That is why I rejected all requests for permission.”
Chris says that the attackers continued to flood his devices with reset notifications for several days, after which he received a call on his phone and the person identified himself as from Apple technical support.
He added, “I told him that I would call them back and hung up. When I called Apple again on the real number, they assured him that whoever I spoke to was not a support employee. They said that Apple very clearly states that it will never initiate outgoing calls to customers unless they ask.” Customer contact him.
The reason for the vulnerability?
The security expert investigated the problem and found that the attackers were using a page on Apple’s website dedicated to resetting the password for the Apple account in case it was forgotten, to send unwanted notifications.
This page requires an email or phone number, and it also contains a CAPTCHA. When you enter the email address, the page displays the last two digits of the phone number associated with the Apple account. Once you enter the phone number and press Send, the user receives a notification requesting to set the password.



Leave feedback about this